![图片[1]-SiteGround Access Log 网站访问日志查看和解读教程 | 歪猫跨境 | WaimaoB2C-歪猫跨境 | WaimaoB2C](https://img.waimaob2c.com/wp-content/uploads/SiteGround-promo-2310-1500-1.png)
SiteGround 注册无法接收短信验证码? 查看问题的解决方法
什么是网站日志
网站日志是一种记录在网站服务器上发生的所有活动的文件。这些日志文件对于网站管理员来说非常重要,因为它们提供了关于网站访问和操作的详细信息。网站日志通常分为两大类:访问日志(Access Logs)和错误日志(Error Logs)。
- 访问日志(Access Logs)记录了网站接收到的每一个HTTP请求的详细信息:包括访问者的IP地址、访问时间、请求的页面或资源、HTTP状态码、传输的数据量等。它可以用来分析网站的流量、访客行为、流行内容、来源网站等。
- 错误日志(Error Logs)记录了网站在处理请求时遇到的所有错误,包括服务器错误(如500内部服务器错误)、客户端错误(如404未找到)、脚本错误等,它对于诊断网站问题、优化性能和提高网站稳定性至关重要。
访问日志通常包含每个访问者的IP地址、访问时间、请求的页面或文件、服务器的响应状态码、引用网站(如果有)和用户代理(即用户的浏览器和操作系统信息)。通过分析这些数据,我们可以:
- 识别可疑的访客:例如,来自同一IP地址的频繁或非正常的访问可能表明恶意活动。
- 监测流量来源:了解哪些网站或搜索引擎将流量引导到您的网站。
- 优化网站性能:识别出现错误或加载缓慢的页面,以改善用户体验。
- 定制内容和营销策略:了解用户偏好和行为,以更好地满足他们的需求。
![图片[2]-SiteGround Access Log 网站访问日志查看和解读教程 | 歪猫跨境 | WaimaoB2C-歪猫跨境 | WaimaoB2C](https://img.waimaob2c.com/wp-content/uploads/siteground-backtobusiness-231001-1.jpg)
如何获取 SiteGround 过去24小时的网站访问日志
打开 Site Tools > Statistics > Access Log 页面。
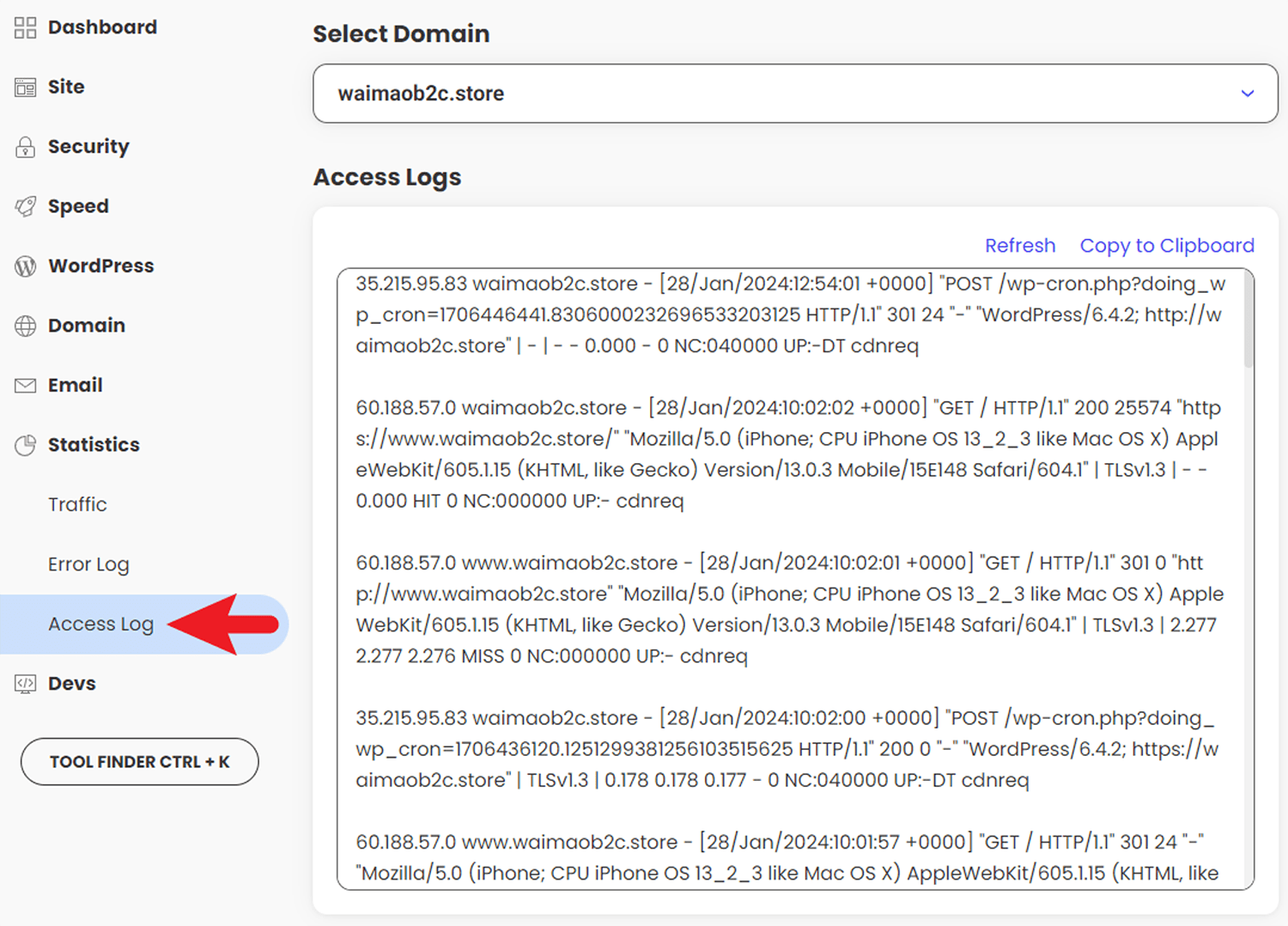
选择要查看日志的网站域名,然后在 Access Logs 中就可以查看到最近24小时的网站访问日志。日志包含了网站每一次访问的详细信息:访问来源的IP地址、时间、请求类型、URI、服务器返回的状态码、引用来源和用户代理。
点击 Refresh 刷新页面查看最新的日志。
点击 Copy to Clipboard 复制所有日志内容到电脑剪切板中。
如何获取 SiteGround 过去30天的网站访问日志
SiteGround 会自动存储过去30天的网站访问日志。
要查看这些日志内容:
打开 Site Tools > Site > File Manager 页面,打开域名文件夹下的 Logs 文件夹,就可以找到过去30天的网站访问日志了。
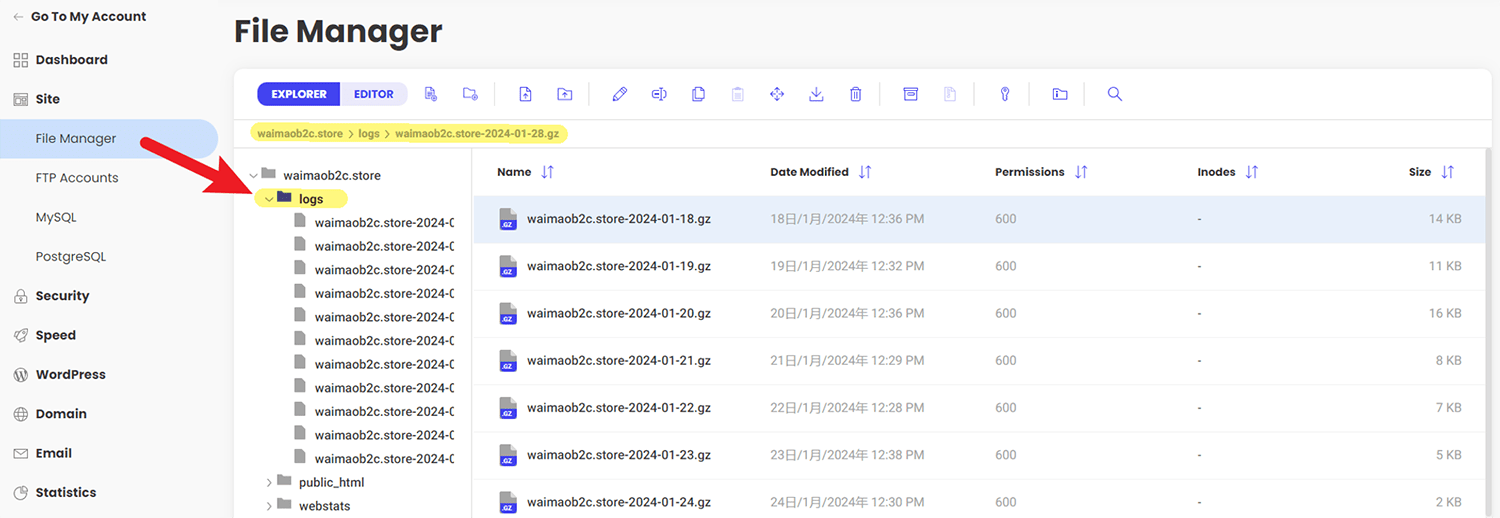
日志文件是 gz 格式的压缩文件,不支持在线查看,右击要下载的日志文件,然后点击 Download,然后在电脑上解压缩文件,使用记事本打开日志文件,就可以查看具体的日志内容了。
如果要下载过去30天所有的日志文件,可以先全选文件,然后点击菜单栏中的 Archive,将所有日志文件打包到一个文件中再下载,或者直接使用 FTP 工具下载,操作上会方便很多。
解读 SiteGround 主机日志文件
网站数据分析我用谷歌分析工具,只有当网站有被攻击的迹象时,如网站宕机,我可能会查看下日志文件,确认攻击源,然后采取相对应的措施。我们可以借助 ChatGPT 对日志文件进行分析。
例如,让 ChatGPT 帮助我们解读某条日志每个字段的含义:
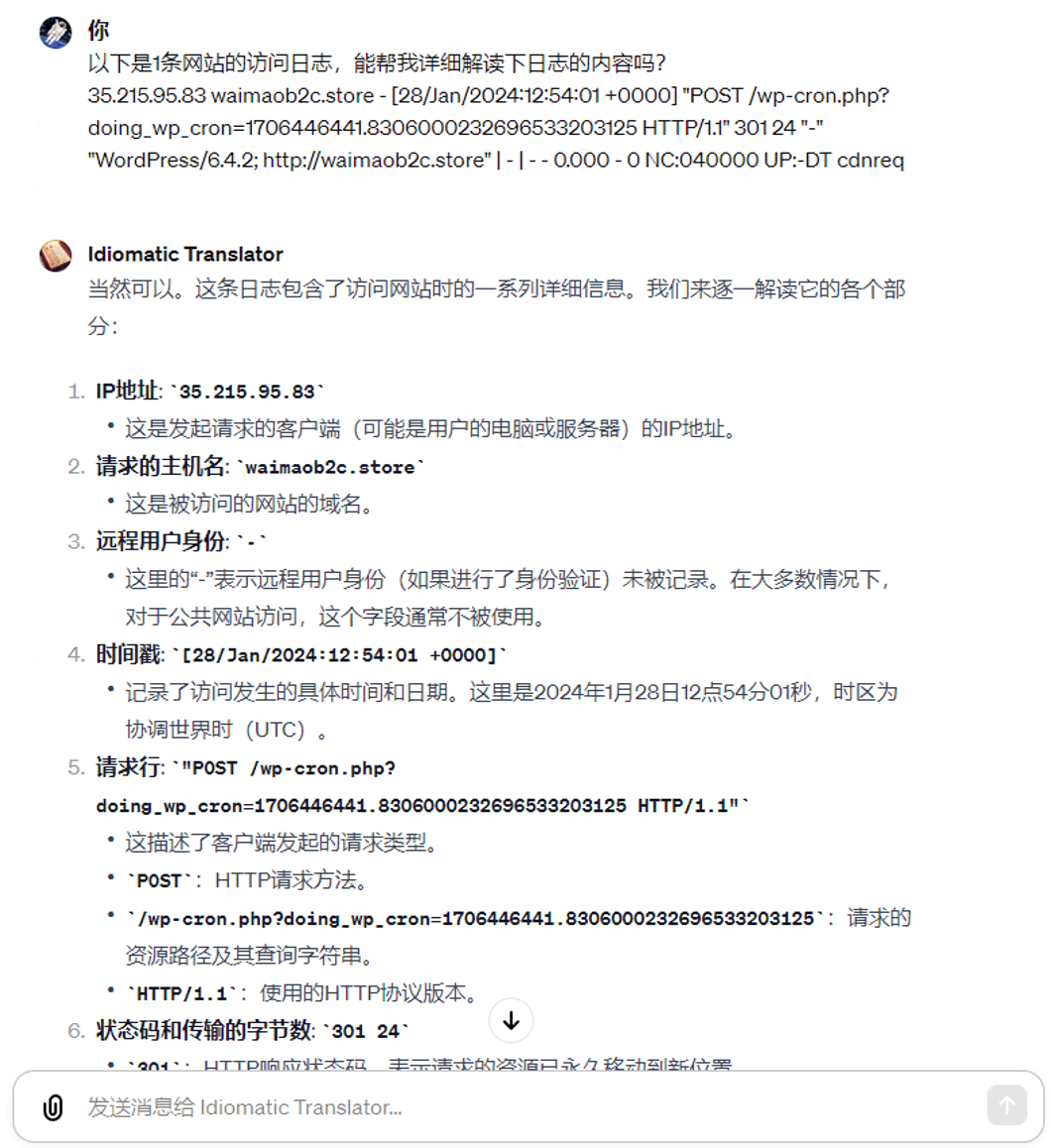
或者借助 GPT Store 里面别人写的 GPTs 分析整个日志内容。
例如 Log Analyzer https://chat.openai.com/g/g-JBmeWsY2w-log-analyzer
我将大段的日志提交给 Log Analyzer 之后,它提供的分析,以及根据分析给出的建议还是很给力的。
内容如下:
Thank you for providing the logs. Let’s analyze them for any abnormal behavior or patterns. The logs seem to be from a web server, capturing various requests to a website. I will examine them for any unusual activities, such as:
- Repeated access attempts from the same IP: Multiple requests in a short time from the same IP can indicate a bot or a scraper.
- Status code anomalies: A high number of 4xx or 5xx status codes could indicate errors or unauthorized access attempts.
- Patterns in request types: An unusual number of specific request types (like POST requests to certain endpoints) might be suspicious.
- User-agent strings: Certain user-agent strings can be associated with known malicious bots or scrapers.
Let’s start by summarizing the data based on these criteria.
Based on the provided log entries, here are some insights:
- IP Addresses:
185.220.238.200made 2 requests. This IP seems to be more active compared to others.135.181.213.220made 1 request.
- Status Codes:
- There were 3 requests with a status code of
200, indicating successful responses. - There was 1 request with a status code of
404, indicating a not found error. This could be normal or indicate broken links or probing for vulnerabilities.
- There were 3 requests with a status code of
- User Agents:
- The user agent
Mozilla/5.0 (Windows NT 10.0; Win64; x64)...was used in 2 requests. This is a common user agent string for browsers, so it seems legitimate. - One request used the user agent
Mozilla/5.0 (compatible; MJ12bot/v1.4.8; <http://mj12bot.com/>). This is a known bot, specifically MJ12bot. - One request used
WordPress/6.4.2; <https://www.waimaob2c.com> as the user agent, which is likely a WordPress cron job or similar internal request.
- The user agent
Observations:
- The high frequency of requests from
185.220.238.200could be worth monitoring, but it’s not necessarily abnormal with this small dataset. - The
MJ12botuser agent indicates a web crawler. It’s generally harmless unless it’s causing a high load on the server. - The
404status code might be worth investigating to ensure there are no broken links or that it’s not a sign of probing for vulnerabilities. - The WordPress related request seems normal and part of the site’s operation.
Recommendations:
- Monitor the
185.220.238.200IP for further activity to rule out any potential scraping or attack attempts. - Check the URLs returning
404to fix any broken links or investigate unauthorized access attempts. - If the
MJ12botis causing high load or unwanted traffic, consider blocking or regulating its access throughrobots.txtor web server configurations.
For a more comprehensive analysis, a larger dataset and access to historical logs would be beneficial. Let me know if there’s anything specific you’re concerned about or if there’s more data to analyze!
![图片[6]-SiteGround Access Log 网站访问日志查看和解读教程 | 歪猫跨境 | WaimaoB2C-歪猫跨境 | WaimaoB2C](https://img.waimaob2c.com/wp-content/uploads/SiteGround-jiaocheng-waimaob2c-2024.png)














暂无评论内容